
FISHY Security & Privacy Dataspace Infrastructure

An enhanced framework for system events' management, including metrics from different sources and promoting co-relation with added semantics
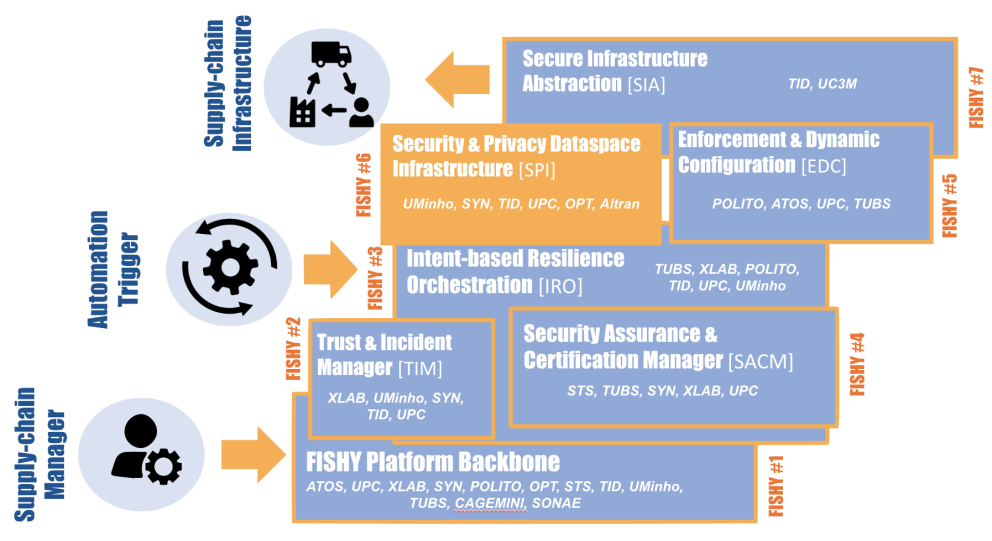
Organizing data related to infrastructure events and enforcing privacy and Access Control rules, including Identity Management. This solution translates high-level intents into configured policies, and interact with the system response using AI techniques.
BENEFITS
1. Access Control (AC) policy and rules definition and enforcement technology.
2. Identity Management strategy, which is fundamental in a supply chain environment where different users' perspectives and demands must coexist.
3. Data sanitization and flow control from low-level on-premise components, according to previously defined privacy rules.
USE CASES
Smart manufacturing - The module will be used to receive from IRO the registration of new IoT devices and keep an updated list of registered devices
Farm-to-fork - The SPI is required to receive the information from the F2F IT systems and pass it to the inner components of the FISHY platform ensuring anonymisation
Autonomous driving - The module will be used to manage user authentication and ensure that requests are secure. It is expected to provide ways to register and authenticate for IoT device and car manufacturers.
Horizon Results Platform ID 42335
| Attachment | Size |
|---|---|
| 1.76 MB | |
| 983.34 KB |
Resources for EU Research
Resources for SMEs
News & Events
Reports
Cyberwatching.eu has received funding from the European Union’s Horizon 2020 research and innovation programme under grant agreement No 740129. The content of this website does not represent the opinion of the European Commission, and the European Commission is not responsible for any use that might be made of such content. Privacy Policy | Disclaimer / Terms and Conditions of Use
