
FISHY Enforcement & Dynamic Configuration

Framework leveraging a capability model instead of the traditional refinement techniques based on logic rules
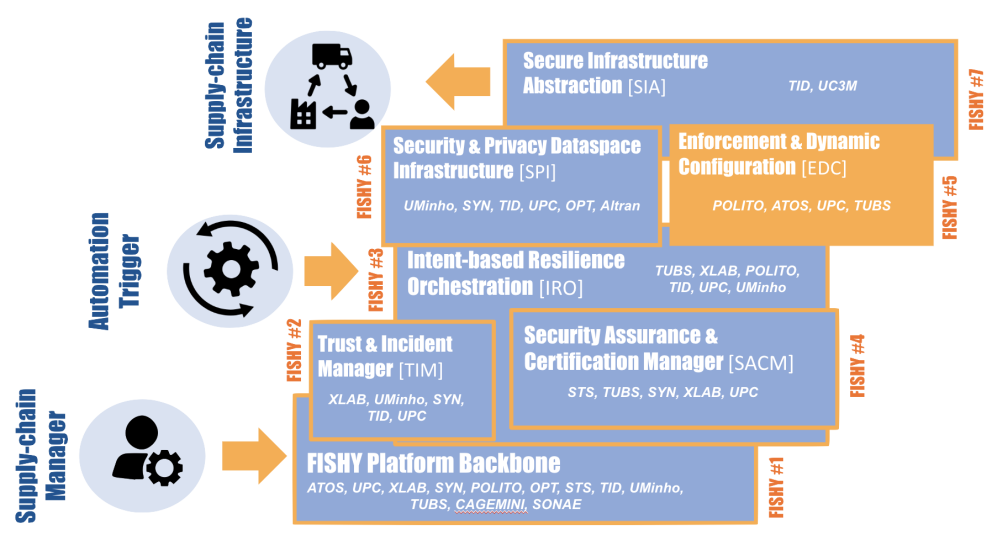
The EDC allows an administrator to effortlessly configure various security controls (e.g., a firewall or a VPN terminator) through high-level declarative policies that are automatically translated into a series of optimal low-level configurations. Its innovative refinement process will consider the current network landscape topology and its configurations to avoid inconsistencies and issues in the deployed rules. Its component architecture is tailored to supply chain needs focusing especially on regulatory obligations (e.g., GDPR) and violations/compliance of service level agreements.
BENEFITS
1. A capability model empowers the core of the EDC, allowing an administrator to add support for new types of security controls with ease. Adding new security devices is performed by describing what they offer (e.g., this device is a stateful firewall, supports traffic rate- limiting) without writing ad-hoc code logic.
2. The use of a high-level policy language grants the administrators the ability to quickly and easily describe what the network functionalities are in a way closer to the human language, without worrying about their actual implementation, which is demanded to the EDC itself.
3. The EDC seamlessly supports both physical and virtualized security controls and allows the administrators to configure mixed networks containing both types of devices.
USE CASES
Smart manufacturing - Will apply security policies to mitigate risks, attacks or intrusions detected, applying security configurations when a non-compliance situation is detected. The request is expected to come from the IRO or the SACM.
Autonomous driving - Mainly used to apply security policies on the infrastructure to mitigate possible risks, attacks or intrusions detected. It applies security configurations when any security policy is not complied with, by request from the IRO or the SACM.
Farm-to-fork - The EDC is required to decide the baning of specific IPs and blockchain wallet IDs when these are issuing an attack; other similar policies may be defined based on the specifics of the IT solutions in place.
Horizon Results Platform ID 42337
| Attachment | Size |
|---|---|
| 1.76 MB | |
| 1.04 MB |
Resources for EU Research
Resources for SMEs
News & Events
Reports
Cyberwatching.eu has received funding from the European Union’s Horizon 2020 research and innovation programme under grant agreement No 740129. The content of this website does not represent the opinion of the European Commission, and the European Commission is not responsible for any use that might be made of such content. Privacy Policy | Disclaimer / Terms and Conditions of Use
